Blogs
Your HPE-Juniper networking install base… and why it’s basically your linen cupboard at home
How is your network install base like your linen cupboard? Stay with me.
Read More

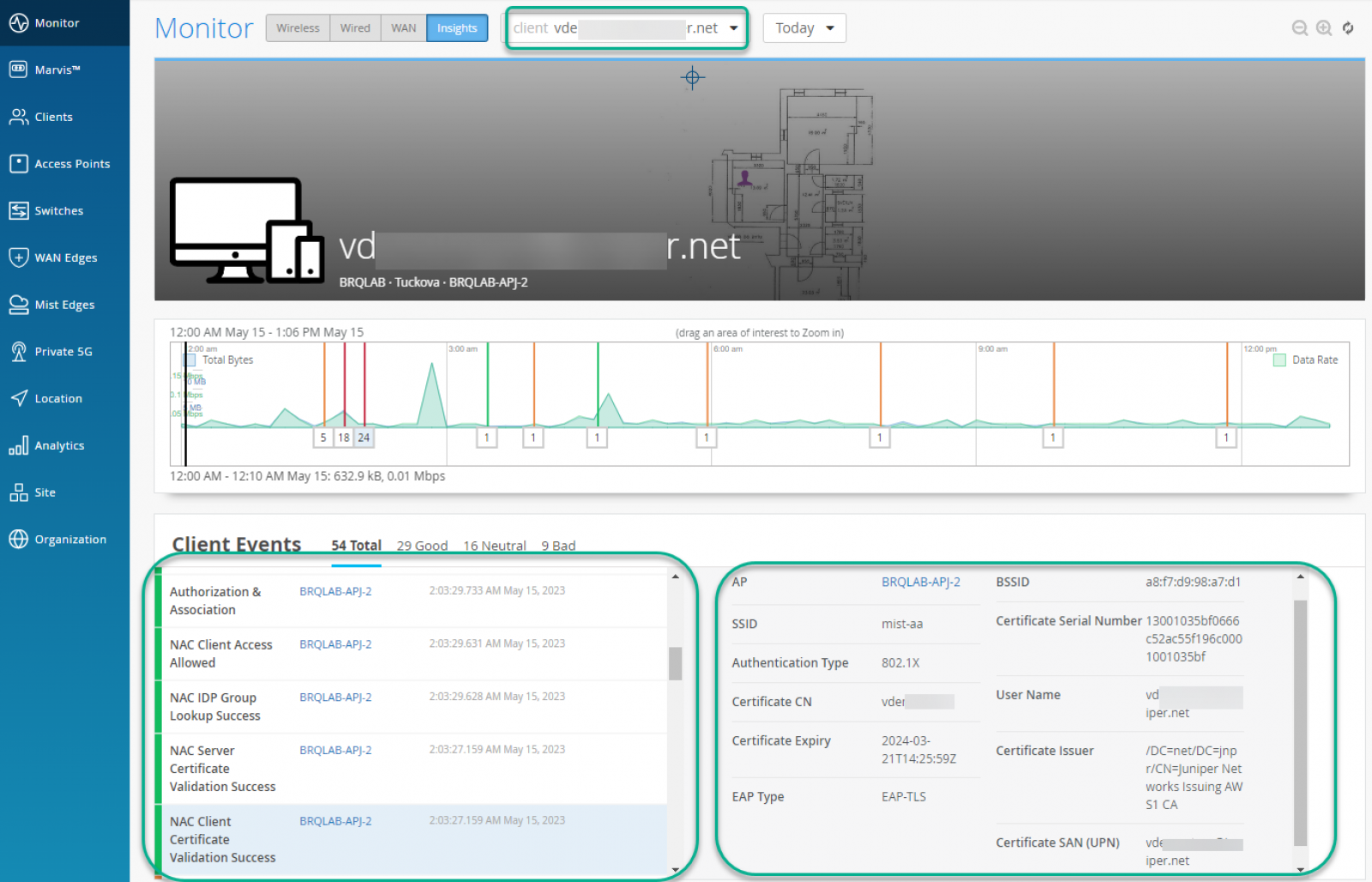
Juniper Mist Access Assurance is a network admission control and access management platform built from the ground up eliminating the need of the typical NAC infrastructure components. This quick start guide will guide users through the steps from enabling Access Assurance to simple troubleshooting.
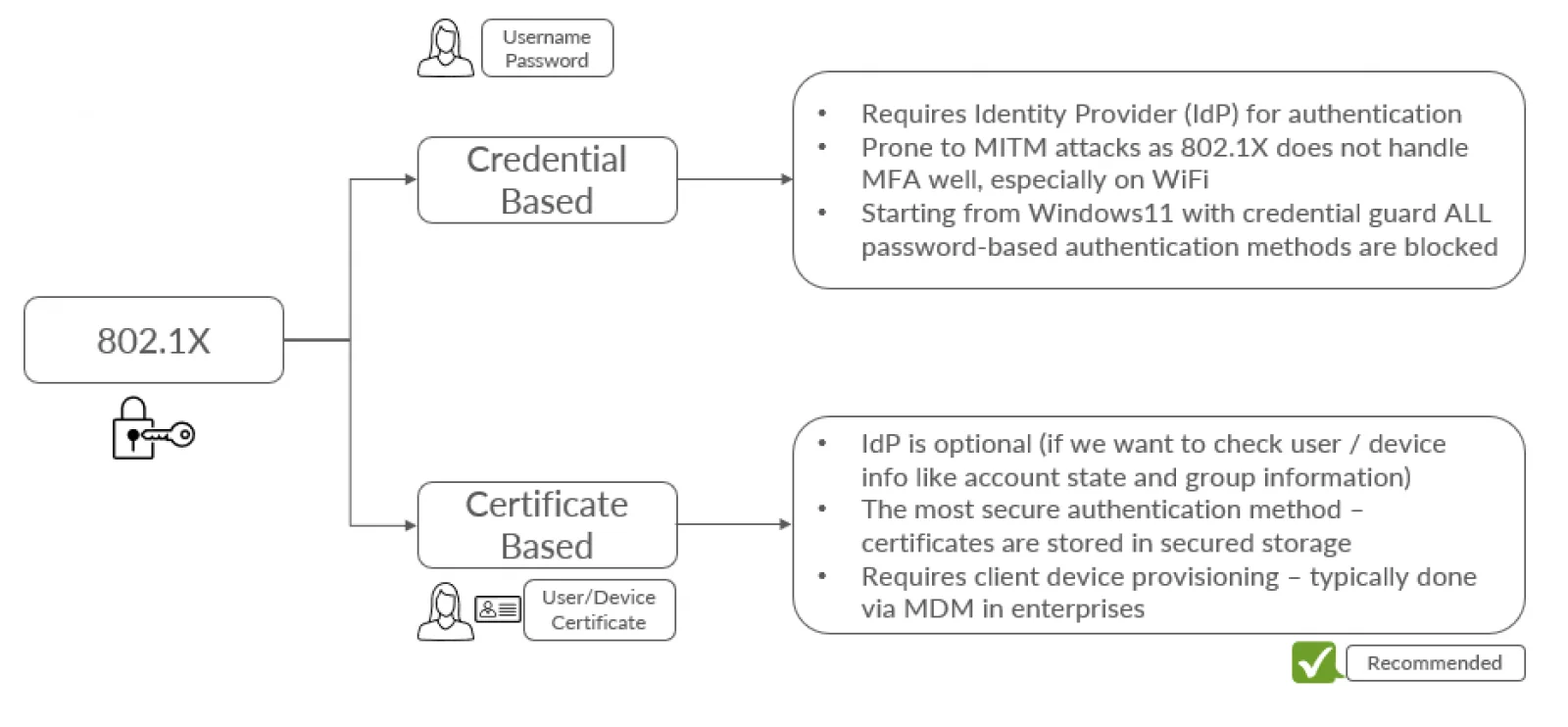
1. 802.1X (Cred & Cert based auth)
The Radius 802.1X authentication enables network operators to automatically authenticate and authorise a user or device and let them into the network. This works with the typical user and device management systems such as Azure Active Directory, Okta, JamF etc.
Certificate based authentication is recommended to future proof the configuration.
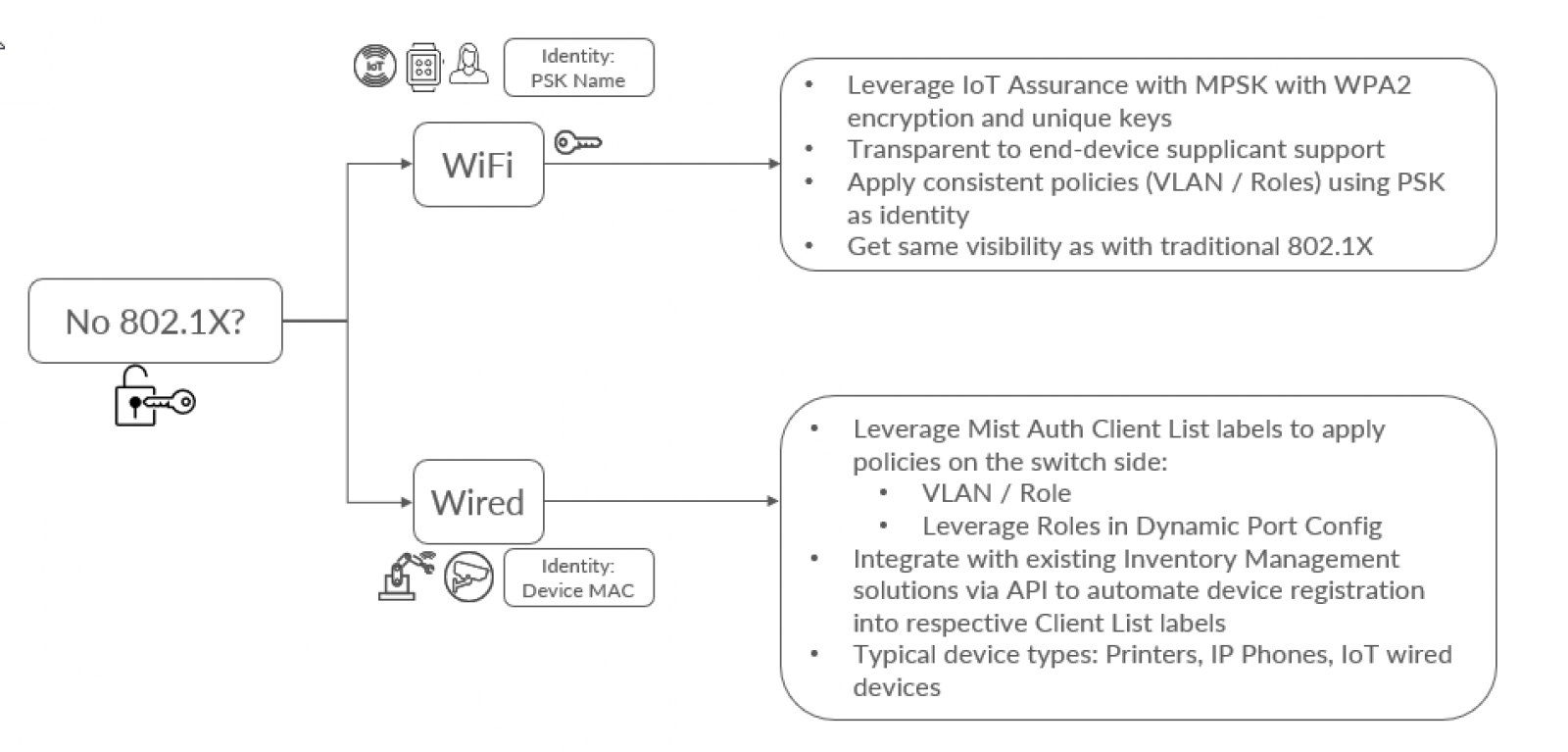
2. Non-802.1X (MAB / MPSK)
This use-case is helpful to onboard devices that do not support 802.1X. Typical devices are IoT devices like security cameras, temperature sensors etc. Also when it comes to wireless devices, in some scenarios like BYOD you want to avoid dealing with 802.1X client provisioning for unmanaged devices, and prefer other simpler onboarding mechanisms.
For such wireless devices Multi-PSK option can be used for wireless devices for both IoT and BYOD scenarios and MAB (MAC Authentication Bypass) option for wired devices.
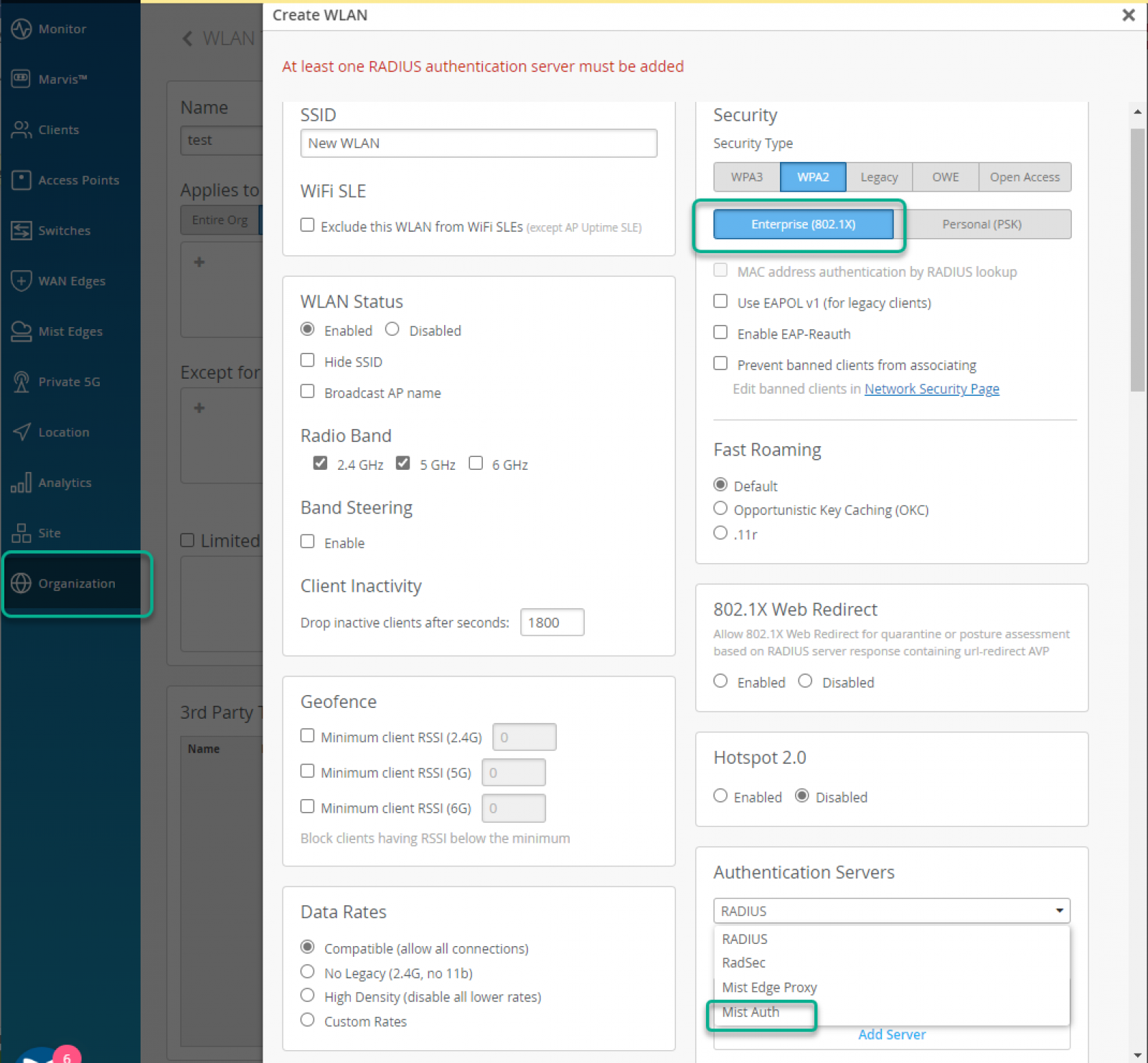
For the wireless devices enable Juniper Mist Access Assurance from the WLAN Templates menu option. Select Security as “Enterprise (802.1X)” (either WPA2 or WPA3) and select Authentication Servers as “Mist Auth”
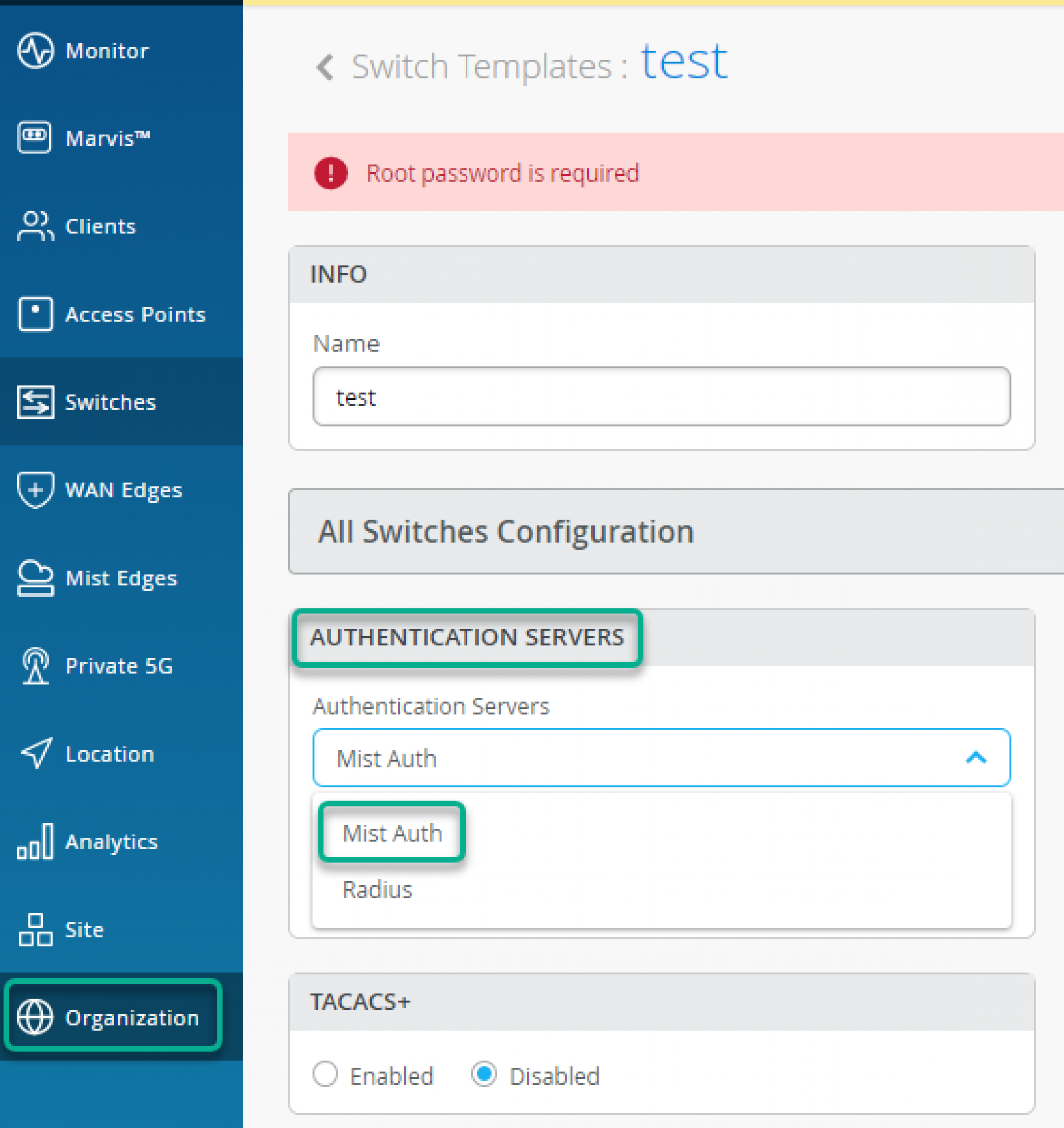
For Wired Clients, Authentication Servers is configured under Wired -> “Switch Templates” option.
Certificates section manages Trusted Certificate Authorities, as well as Mist Access Assurance Server Certificate configuration.
In order for EAP-TLS certificate-based authentication to work, you must add trusted Certificate Authority into the Mist dashboard, this will let Mist Auth service trust client certificates signed by added CAs.
Trusted CA Certificates can be added from the Organization -> Access -> Certificates -> Add Certificate Authority page.
CA Certificates can be directly pasted and system will automatically parse and decode imported CA cert. We recommend to add your Root CA, as well as all your Intermediate or Issuing CA certificates one by one.
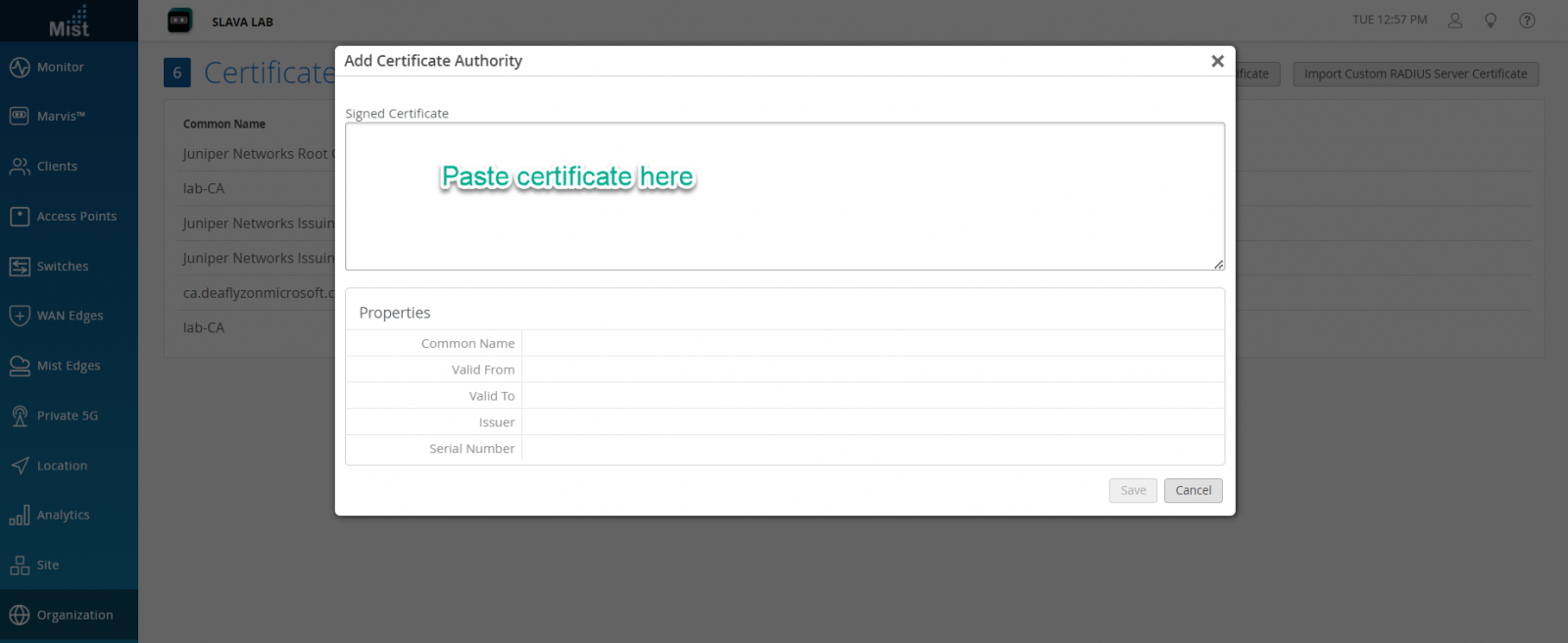
Identity Providers can be used to either get additional identity context for clients authenticated via certificates or IDPs can also authenticate clients when they are using password based authentication via EAP-TTLS/PAP
Identity providers can be configured from Organization -> Access -> Certificates -> Identity Providers page. This step is optional for EAP-TLS (cert) authentication and it is mandatory in case of EAP-TTLS (credential based) authentication.
Identity providers serve as authentication source (in case of EAP-TTLS) and authorization source (by obtaining user group memeberships, account state etc) for EAP-TLS or EAP-TTLS.
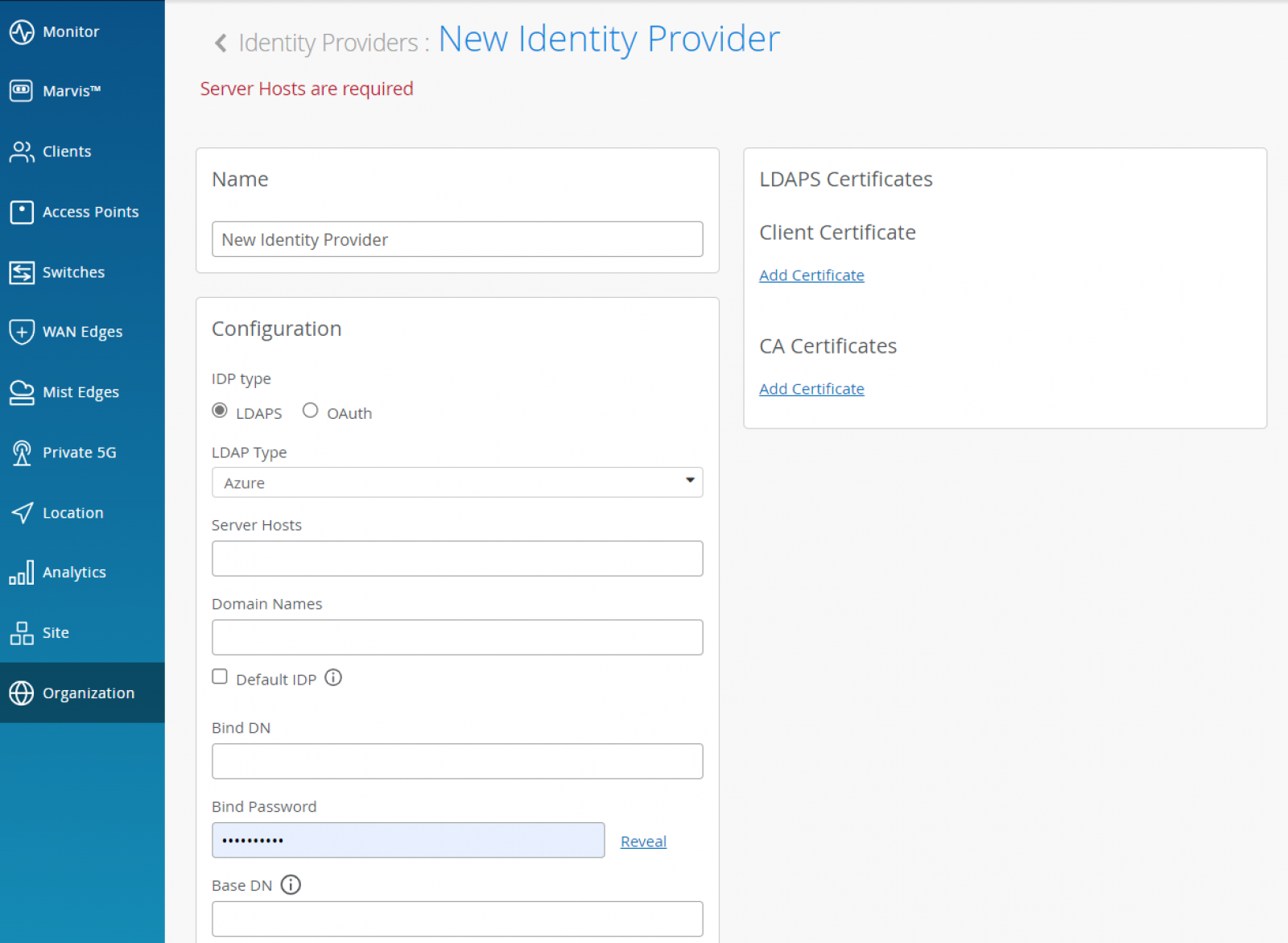
Auth Policies leverage labels to determine the identity signature of the client device in order to decide whether network access should be allowed, and which additional attributes (like VLAN, Role, GBP Tag) needs to be applied. Labels can be matching criteria or the actions that need to be performed after the match.
Labels can be created directly from the Organization > Access > Auth Policies page or from the Organization > Access > Auth Policy Labels menu. Click on “Add Label” to add a matching criteria or action.
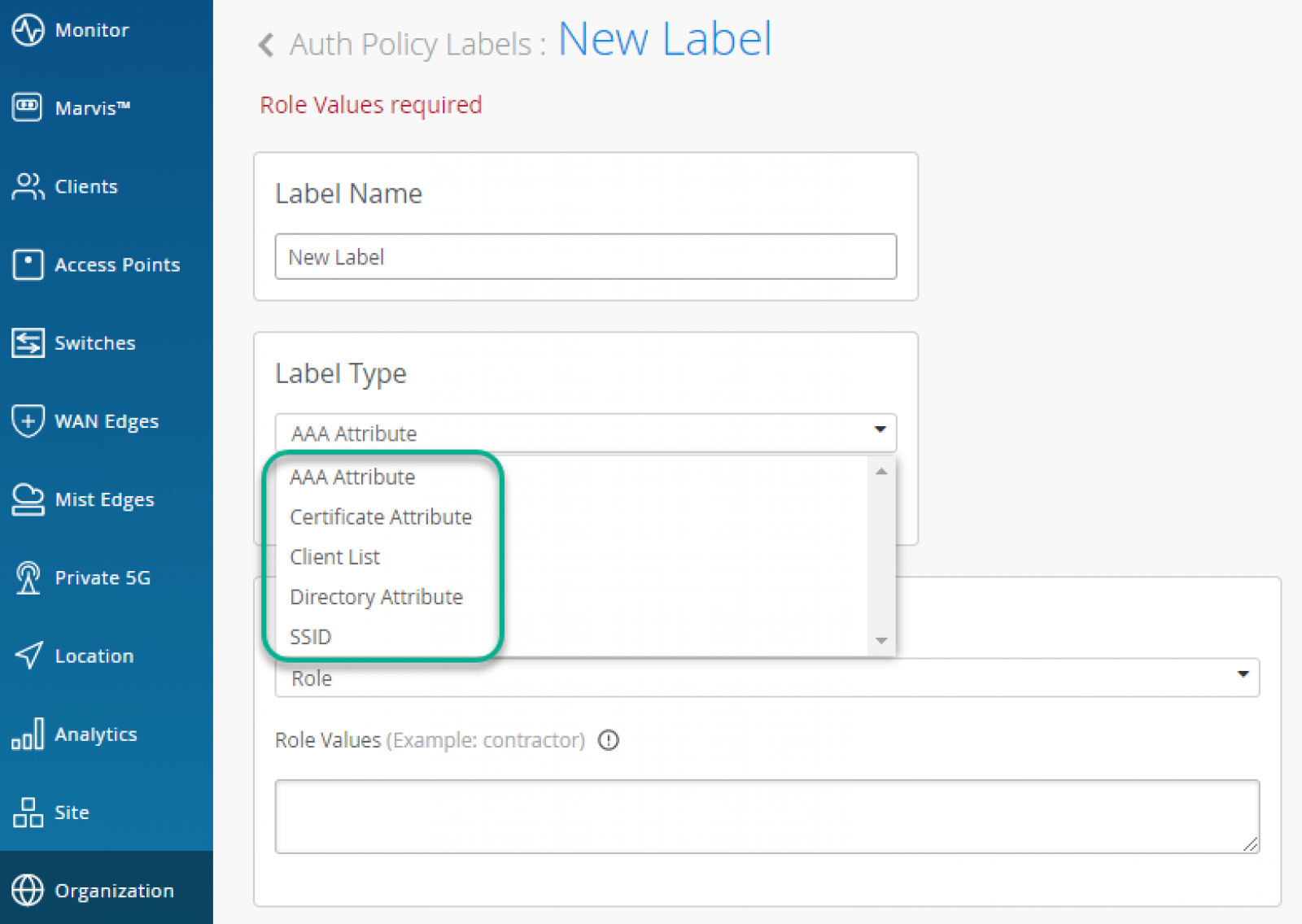
You can match users or devices based on the following criteria:
After a user or device has matched a specific rule, you can assign following actions:
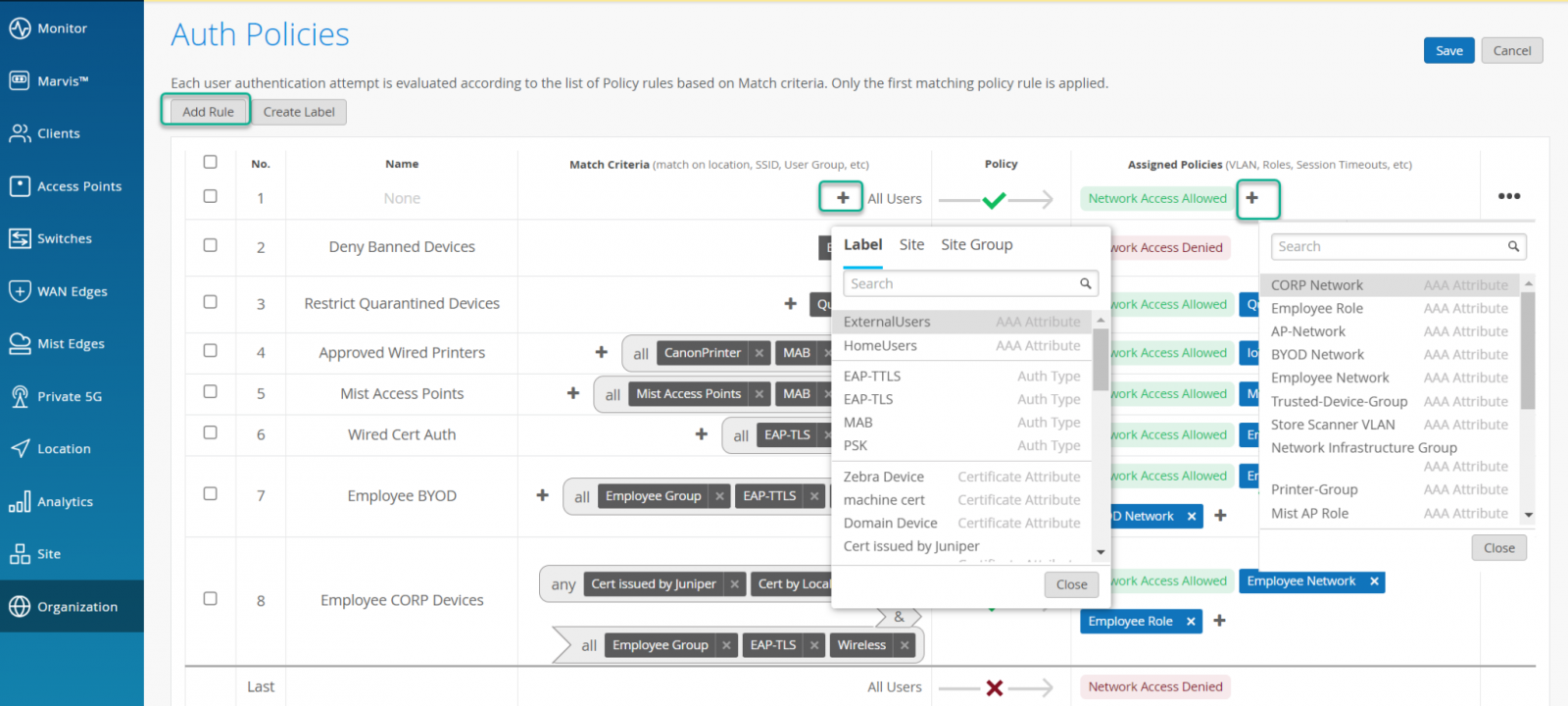
Auth Policies can be created from Organisation > Access > Auth Policies menu. New Rules can be added by clicking on the “Add Rule” option and choosing Match Criteria and Assigned Policies.
All client events from both the network side and Access Assurance site are under Client Insights.
Blogs
How is your network install base like your linen cupboard? Stay with me.
Read More
Blogs
A recent ED trip with one of the kids revealed a surprisingly accurate triage wait-time counter. I expected a feel-good dummy number — but nope, it actually worked.
Read More
Technical
Whether you're just stepping into the world of monitoring or you've been staring at Zabbix dashboards for years, it helps to understand how all the pieces fit together. Zabbix relies on a few key components—like servers, agents, and proxies—to keep an eye on your environment. Here's a quick...
Read More